This article describes how to filter automation stitch triggers for FortiGate events based on log parameters.
Solution
As some of the events that trigger an automation stitch can cause excessive or unwanted messages/actions, the CLI filtering option can help mitigate this issue.
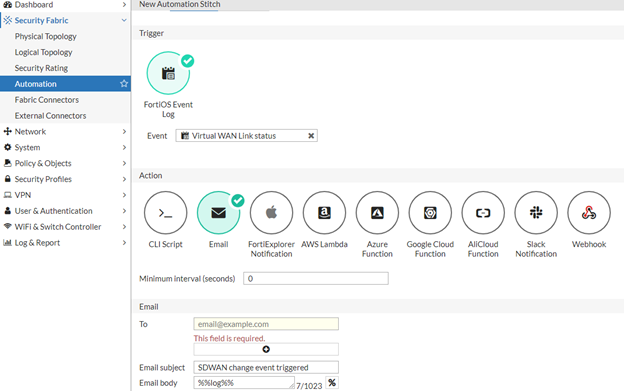
Create an automation stitch that will trigger an email to be send, based on a FortiOS event:
- Go to Security Fabric -> Automation and select 'Create New'.
- Enter Name, choose Triggering event – in this case FortiOS Event Log.
- Choose action Email and configure the email details – Recipients (TO), subject and body.
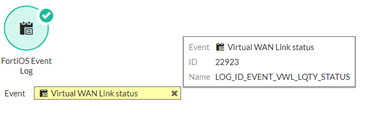
This type of event can be triggered by multiple factors, as seen in the Message column:
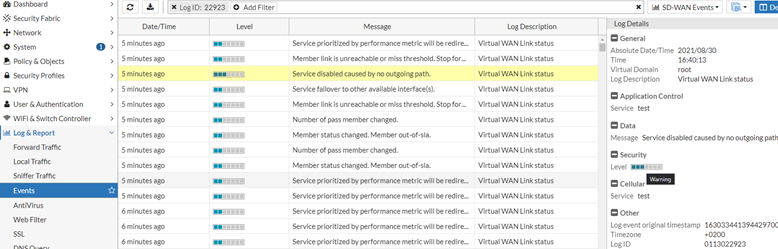
Please follow the steps below to update the filters:
- Go to the field filters and add a filter column with "healthcheck" equal to the required "Performance SLA Name."
- Add another column with "msg" equal to "Member status changed. Member out-of-sla."
Note: Please ensure that the value "Member status changed. Member out-of-sla." is retained in its entirety, including the dot at the end.
Reference screenshot:

Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article